Malware lab
Assemblyline
Source: assemblyline
Inspired from a good colleague, i have made this installation guide for you to test the malware lab out. Be aware this is not a full comprehensive guide, but more a getting started.
What you need to try it out?
I have tested this on a virtual server running 32 GB of RAM, 16 cores and 360 GB of diskspace. This has proven to be fine for testing this out for my part. maybe less hardware can support a test, i havent tried this out to be honest. Im running the Hetzner server CX53, wich has proven an excelen choice and good for the price
The operating system is an updated version of Ubuntu 24:04, latest docker version
Source: https://docs.docker.com/engine/install/ubuntu/
Add Docker's official GPG key:
sudo apt-get update
sudo apt-get install ca-certificates curlsudo install -m 0755 -d /etc/apt/keyringssudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.ascsudo chmod a+r /etc/apt/keyrings/docker.ascAdd the repository to Apt sources
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/ubuntu \
$(. /etc/os-release && echo "${UBUNTU_CODENAME:-$VERSION_CODENAME}") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/nullsudo apt-get updateInstall the packages
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginsudo systemctl status dockersudo systemctl start dockersudo docker run hello-worldInstall assemblyline
Now the server is ready for installing assemblyline on the system.
Source for inspiration : https://cybercentrecanada.github.io/assemblyline4_docs/installation/deployment/
git clone https://github.com/CybercentreCanada/assemblyline-docker-compose.git ~/deployments/assemblylinecd ~/deployments/assemblyline.env file
When that is downloaded and you are in the right folder, you need to ajust the .env file. Below are the file that is have ajusted. remember to set in strong passwords and choose the installation minimum or full
# Choose your the service release channel: stable or latest
# NOTE: This is only used once during the bootstrap process
SERVICE_VERSION=4.6.stable
# Pick the version of assemblyline you which to run
# NOTE: You can also lock it down to a specific version if you want
AL_VERSION=4.6.0.stable18
# If the appliance is going to have a domain name include it here
DOMAIN=assemblyline.local
# Replace these with real passwords
FILESTORE_PASSWORD=<STRONG PASSWORD>
ELASTIC_PASSWORD=<STRONG PASSWORD>
SERVICE_API_KEY=<STRONG PASSWORD>
# Pick the default admin user/password
# NOTE: this is only used in the bootstrap process
AL_ADMIN_USER=adminuser
AL_ADMIN_PASSWORD=<STRONG PASSWORD>
# Kibana username/password
KIBANA_USERNAME=adminuser
KIBANA_PASSWORD=<STRONG PASSWORD>
# Amount of memory allocated to elasticsearch
ELASTIC_MEM=2048
# Parameter for remote deployments or other cases where files aren't going to be in their normal location
COMPOSE_ROOT=.
# Where do you want docker to find container images? (leave blank unless doing some kind of offline install)
REGISTRY=
# The prefix given to privileged images followed by a "_"
COMPOSE_PROJECT_NAME=al
COMPOSE_PROFILES=full
You can make your selfsigned cert
openssl req -nodes -x509 -newkey rsa:4096 -keyout ~/deployments/assemblyline/config/nginx.key -out ~/deployments/assemblyline/config/nginx.crt -days 365 -subj "/C=CA/ST=Ontario/L=Ottawa/O=CCCS/CN=assemblyline.local"
Now you need to run the docker installation
cd ~/deployments/assemblyline
sudo docker compose pull --ignore-buildable
sudo env COMPOSE_BAKE=true docker compose build
sudo docker compose -f bootstrap-compose.yaml pullcd ~/deployments/assemblyline
sudo docker compose up -d --wait
sudo docker compose -f bootstrap-compose.yaml upCongratulations, now you should have a server running assembly line
Interface

Here you can choose you file analysis and the modes you like to test.
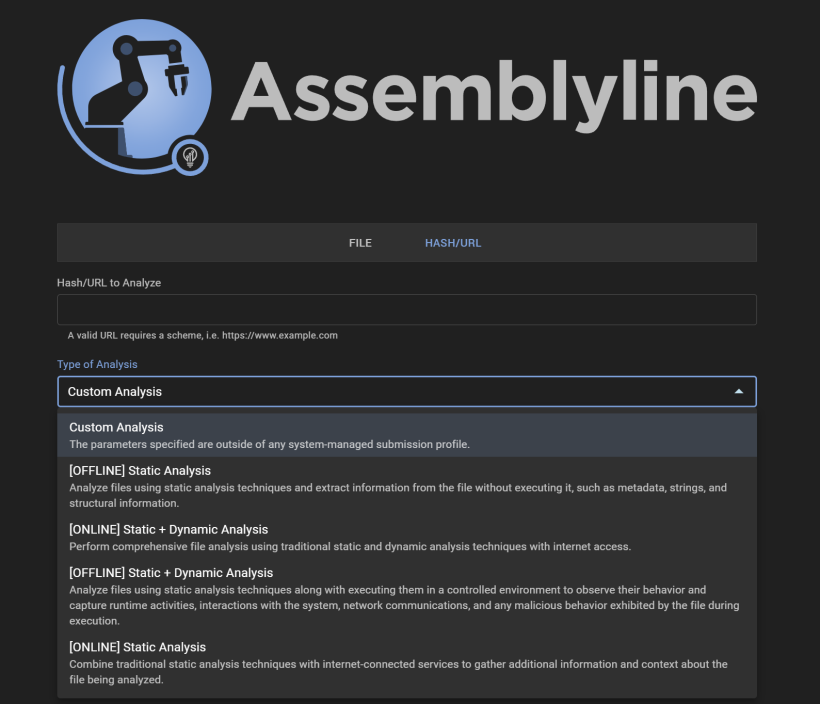
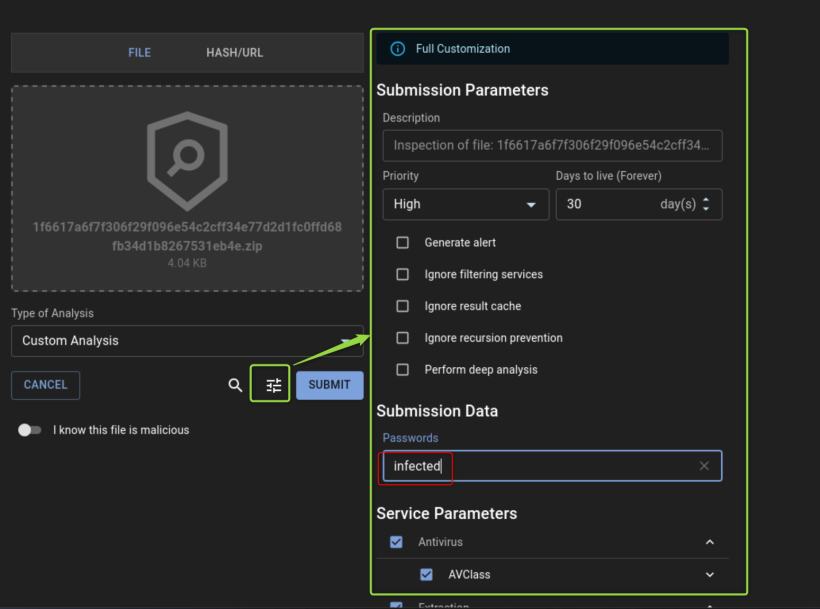
When you submit a file, this needs to run for some time, depending on the mode you run and the modules you run. if you choose the below button, you get a little more settings for submitting the file. Be aware you will get a warning for using online analysis.
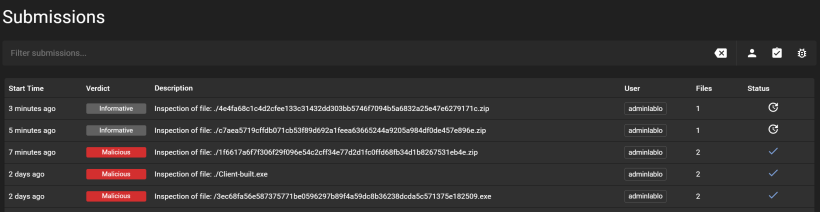
This is the report from the above selection. You start with a simple view, and from there you can choose report view
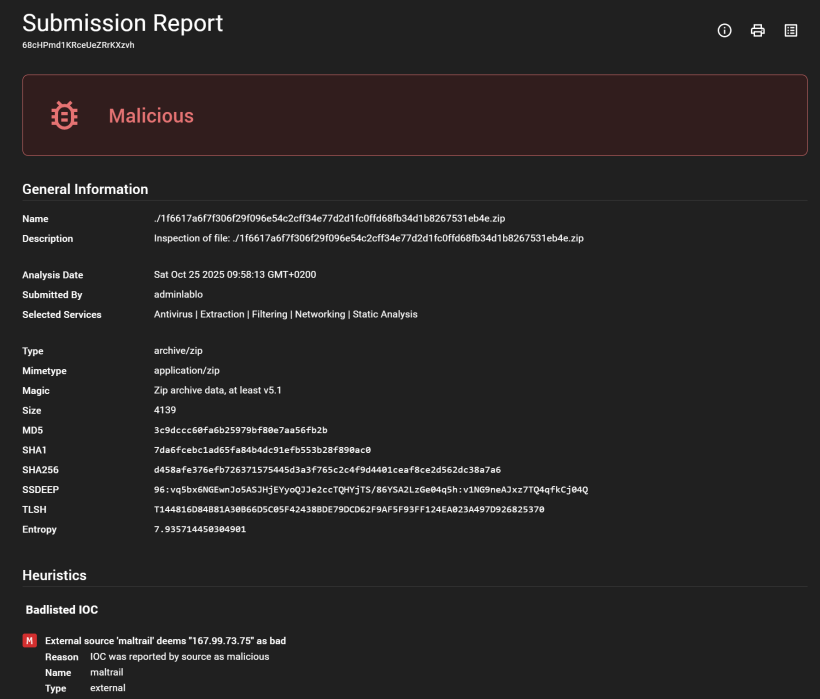
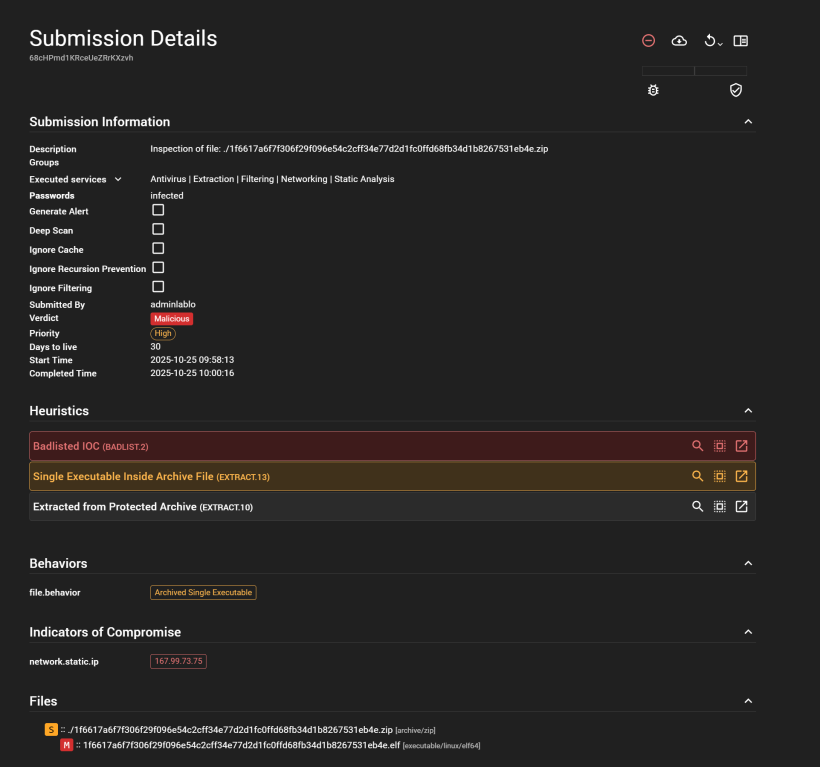
You can expand the above selection for more details of the source of information
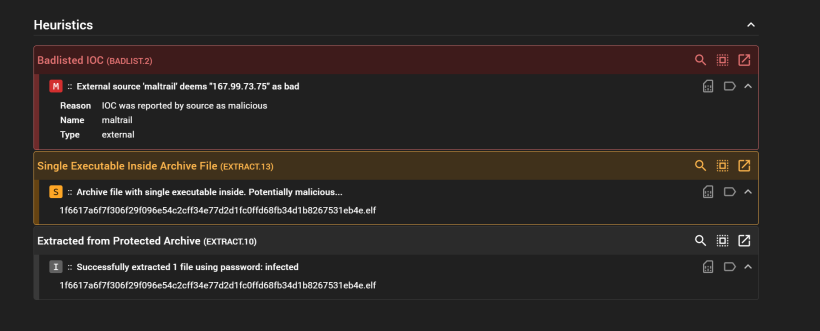
If you press on the icon to the far east, the square with arrow upright. you get the details and some more soruces of information from malware bazaar
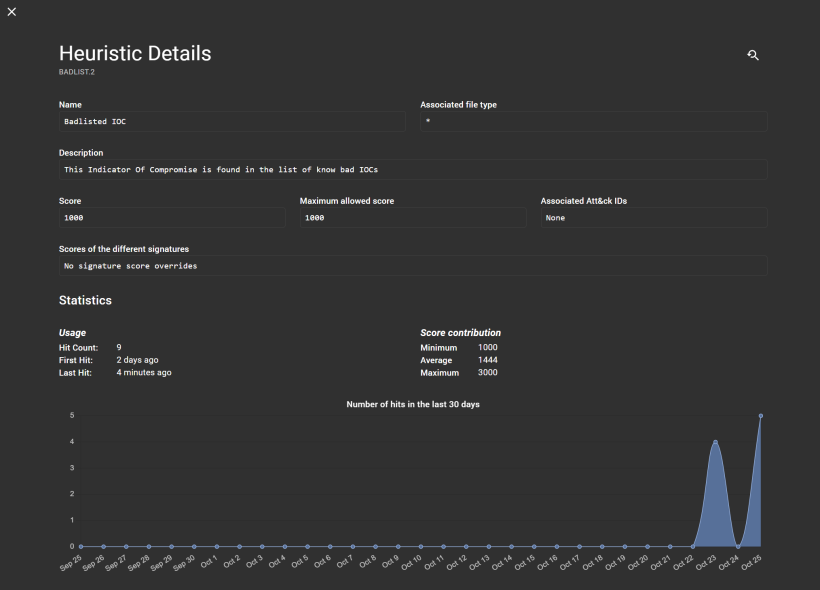
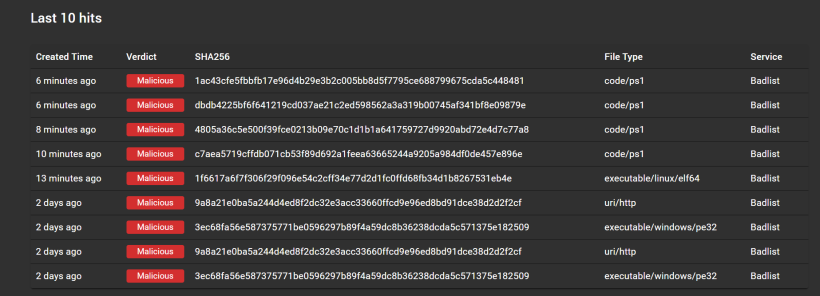
From there you can see the data from malwarebazaar beeing displayed there. Quite cool to see the submissions similar to the sample you have.
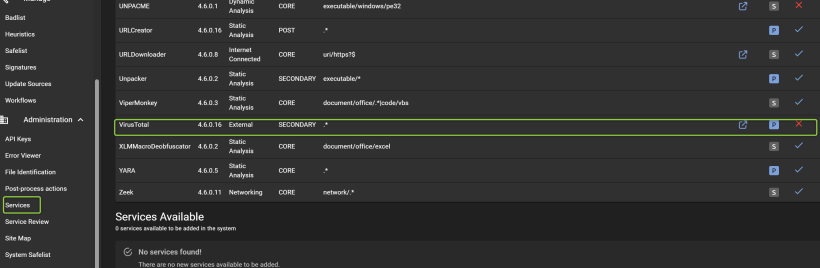
Below you can choose management and sources for updates. This will run during the day, so they will be updated
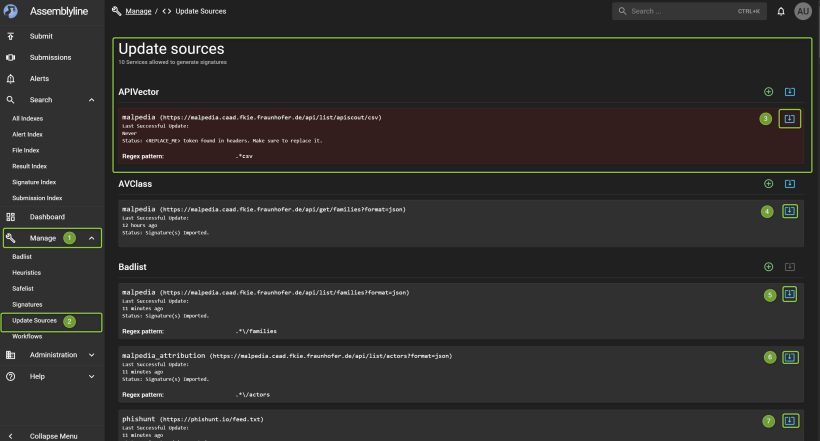
You can install community service for further analysis. In the time of writing im not sure if data are shared ? so be carefull here :)
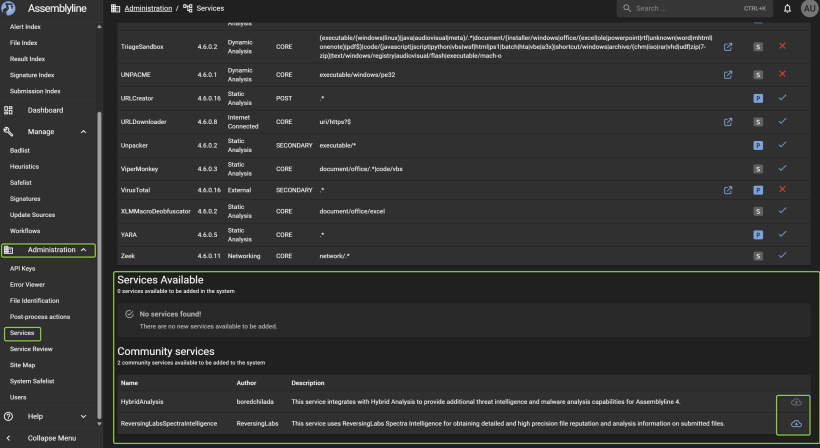
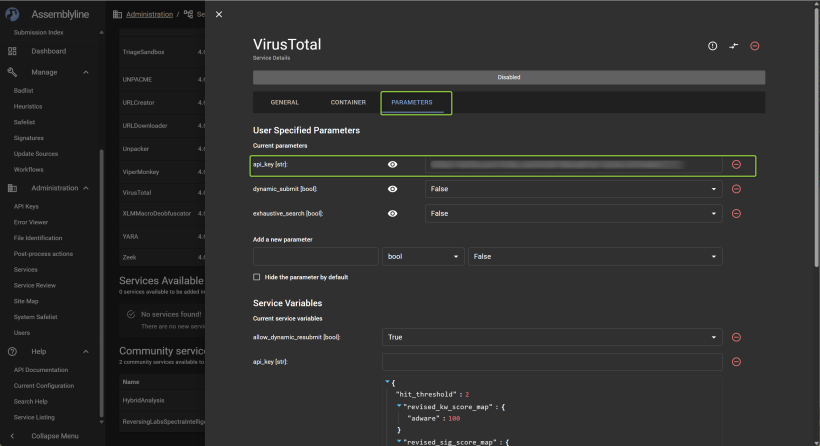
Under servicelist you can see the active services running and the red ones that dosent. However you can choose services and see the list, from there you can edit the services and the function. You can also add API keyes for the service you connect to fx virustotal, and you can choose if you shall submit the file. Again be aware here!